Popular x64 Tags
- internet x64 download
- delete x64 download
- cookies x64 download
- password x64 download
- lock x64 download
- hide x64 download
- keylogger x64 download
- shredder x64 download
- wipe x64 download
- history x64 download
- security x64 download
- clean x64 download
- protect x64 download
- cache x64 download
- data x64 download
- files x64 download
- secure x64 download
- erase x64 download
- privacy x64 download
- lost password x64 download
- software x64 download
- file x64 download
- utility x64 download
- recovery x64 download
- forgotten password x64 download
- erase history x64 download
- shred x64 download
- remove x64 download
- registry repair programs x64 download
- evidence x64 download
Nessus 10.7.4
Sponsored links:
Tenable Network Security, Inc.
Nessus is a complete and very useful network vulnerability scanner which includes high-speed checks for thousands of the most commonly updated vulnerabilities, a wide variety of scanning options, an easy-to-use interface, and effective reporting.
The versatile Nessus® vulnerability scanner provides patch, configuration, and compliance auditing; mobile, malware, and botnet discovery; sensitive data identification; and many other features.
With a continuously updated library of more than 60,000 plugins and the support of Tenable’s expert vulnerability research team, Nessus delivers accuracy to the marketplace. Nessus provides multi-scanner support, scales to serve the largest organizations, and is easy to deploy on premise or in the Amazon Web Services (AWS) cloud.
Heartbleed
Tenable Products Provide Strategic Solutions
The significance of CVE-2014-0160, aka Heartbleed, an attack against the transport layer security protocol (TLS/DTLS) heartbeat extension, is well documented. What could use more discussion is what it really takes to find all vulnerable systems in today's networks.
The vulnerability exists in the OpenSSL library, widely used by Linux operating systems, embedded systems and most applications implementing SSL encryption
While you can patch the vulnerability in your operating system, the vulnerable library can be built into the application, as it is with OpenVPN and other applications which must also be patched
The vulnerability can present itself in any service which implements SSL, allowing it to exist in services other than HTTPS (port 443), including email, instant messenger, and many other common (and uncommon) services and applications
Once you’ve patched the vulnerability on all of the systems and services you’ve discovered, it can easily be re-introduced if someone installs a vulnerable application or embedded system that has not yet been patched (or an older version where the vulnerability exists).
Through a comprehensive set of plugins and dashboards delivered within hours of the discovery of this vulnerability, Tenable customers were able to identify risk from Heartbleed across a wide variety of infrastructure, systems, and applications.
Nessus Perimeter Service
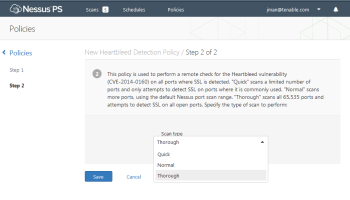
If you are concerned with your Internet facing systems, particularly your web sites or VPN connections, you may use the same Nessus Heartbleed detection policy wizard to create a schedule for scanning your systems from our remote, cloud-based vulnerability scanner, the Nessus® Perimeter Service™.
Nessus Perimeter Service can be used to check for the for the Heartbleed vulnerability using one or more of the following three settings:
Quick – limited to searching for ports/services that are known to use OpenSSL;
Normal – searches for the vulnerability on the Nessus default set of ports; or
Thorough – performs a comprehensive sweep of all 65K ports and detects use of SSL.
Nessus Perimeter Service allows for unlimited scanning of unlimited IP addresses and will help you discover where SSL communications that rely on OpenSSL are entering into your network, and whether they are vulnerable to the heartbeat attack.
PVS – Passive Scanning
For those hard to reach places, Tenable’s Passive Vulnerability Scanner™ (PVS™) can sniff the network and identify hosts vulnerable to the “Heartbleed” attack.
PVS is a powerful tool for finding Heartbleed and other vulnerabilities which may escape some traditional detection methods. By passively monitoring network traffic, PVS detects server and client vulnerabilities, applications, and connections.
As a data source for SecurityCenter Continuous View™, or as an individual subscription installation, PVS provides valuable insight into Heartbleed and other OpenSSL issues. Shown is a sample report displayed in the PVS web interface.
The versatile Nessus® vulnerability scanner provides patch, configuration, and compliance auditing; mobile, malware, and botnet discovery; sensitive data identification; and many other features.
With a continuously updated library of more than 60,000 plugins and the support of Tenable’s expert vulnerability research team, Nessus delivers accuracy to the marketplace. Nessus provides multi-scanner support, scales to serve the largest organizations, and is easy to deploy on premise or in the Amazon Web Services (AWS) cloud.
Heartbleed
Tenable Products Provide Strategic Solutions
The significance of CVE-2014-0160, aka Heartbleed, an attack against the transport layer security protocol (TLS/DTLS) heartbeat extension, is well documented. What could use more discussion is what it really takes to find all vulnerable systems in today's networks.
The vulnerability exists in the OpenSSL library, widely used by Linux operating systems, embedded systems and most applications implementing SSL encryption
While you can patch the vulnerability in your operating system, the vulnerable library can be built into the application, as it is with OpenVPN and other applications which must also be patched
The vulnerability can present itself in any service which implements SSL, allowing it to exist in services other than HTTPS (port 443), including email, instant messenger, and many other common (and uncommon) services and applications
Once you’ve patched the vulnerability on all of the systems and services you’ve discovered, it can easily be re-introduced if someone installs a vulnerable application or embedded system that has not yet been patched (or an older version where the vulnerability exists).
Through a comprehensive set of plugins and dashboards delivered within hours of the discovery of this vulnerability, Tenable customers were able to identify risk from Heartbleed across a wide variety of infrastructure, systems, and applications.
Nessus Perimeter Service
If you are concerned with your Internet facing systems, particularly your web sites or VPN connections, you may use the same Nessus Heartbleed detection policy wizard to create a schedule for scanning your systems from our remote, cloud-based vulnerability scanner, the Nessus® Perimeter Service™.
Nessus Perimeter Service can be used to check for the for the Heartbleed vulnerability using one or more of the following three settings:
Quick – limited to searching for ports/services that are known to use OpenSSL;
Normal – searches for the vulnerability on the Nessus default set of ports; or
Thorough – performs a comprehensive sweep of all 65K ports and detects use of SSL.
Nessus Perimeter Service allows for unlimited scanning of unlimited IP addresses and will help you discover where SSL communications that rely on OpenSSL are entering into your network, and whether they are vulnerable to the heartbeat attack.
PVS – Passive Scanning
For those hard to reach places, Tenable’s Passive Vulnerability Scanner™ (PVS™) can sniff the network and identify hosts vulnerable to the “Heartbleed” attack.
PVS is a powerful tool for finding Heartbleed and other vulnerabilities which may escape some traditional detection methods. By passively monitoring network traffic, PVS detects server and client vulnerabilities, applications, and connections.
As a data source for SecurityCenter Continuous View™, or as an individual subscription installation, PVS provides valuable insight into Heartbleed and other OpenSSL issues. Shown is a sample report displayed in the PVS web interface.
OS: Windows 7, Windows 7 x64, Windows 8, Windows 8 x64, Windows 10, Windows 10 x64, Windows 11, Linux, Mac OS X
Requirements: macOS (11.0 - 12.0)
Add Your Review or 64-bit Compatibility Report
Top Other 64-bit downloads
Privacy Eraser Portable 6.14.2
Clean up all your Internet history and past computer activities with one click.
Freeware
Wifi Credentials Viewer 1.0.0.7
The best tool to enumerate and fetch all stored Wi-Fi credentials., Created by M
Shareware | $29.00
TorGuard 4.8.9
TorGuard VPN Service encrypts your internet access and provides an anonymous IP
Trialware | $9.99
tags: torrent, privacy, protect, secure, data, encryption, VPN client, anonymous browsing, anonymize connection, hider, hide, VPN
Privacy Eraser Free 6.14.2
Clean up all your Internet history and past computer activities with one click.
Freeware
Members area
Top 64-bit Downloads
-
OpenVPN x64 2.6.11
x64 open source download -
Система видеонаблюдения
Visec 8.0.1.13
x64 freeware download -
The Enigma Protector x64 7.70
x64 demo download -
NOD32 Antivirus (64 bit) 17.1.11.0
x64 trialware download -
ArmorTools Professional
x64 24.12.1
x64 shareware download -
Secret Disk 304.00
x64 freeware download -
TorGuard 4.8.9
x64 trialware download -
COMODO Internet Security
(64 bit) 12.3.4.8032
x64 freeware download -
Prevent Restore 104.00
x64 freeware download -
VSCryptoHash 64-bit 2.5.3.509
x64 freeware download
Top Downloads
-
NordVPN 7.28.4.0
demo download -
CmosPwd 5.0
freeware download -
Malwarebytes Chameleon 3.1.33.0
freeware download -
OpenVPN x64 2.6.11
open source download -
NordPass 5.23.12
trialware download -
DewVPN unlimited free
VPN for Windows 1.2.0.318
freeware download -
Smadav 2023 Rev15.1
freeware download -
Система видеонаблюдения
Visec 8.0.1.13
freeware download -
Asterisk Password Spy 12.0
freeware download -
Aiseesoft Android
Unlocker 1.0.52
shareware download -
Password Decryptor for
IMVU 4.0
freeware download -
Privacy Eraser Portable 6.14.2
freeware download -
BlockSmart 1.0.2.8
freeware download -
NOD32 Antivirus (64 bit) 17.1.11.0
trialware download -
The Enigma Protector x64 7.70
demo download